[Paper Review]
“PLLM-CS: Pre-trained Large Language Model (LLM) for cyber threat detection in satellite networks”
Context: Current satellite networks are susceptible to intrusions
Proposal: a pre-trained Large Language Model for Cyber Security, for short PLLM-CS, which is a variant of pre-trained Transformers, which includes a specialized module for transforming network data into contextually suitable inputs. This transformation enables the proposed LLM to encode contextual information within the cyber data.
Dataset: UNSW_NB 15, TON_IoT. These are not satellites network traffic datasets, but still the authors use them quoting “similarity” reasons …
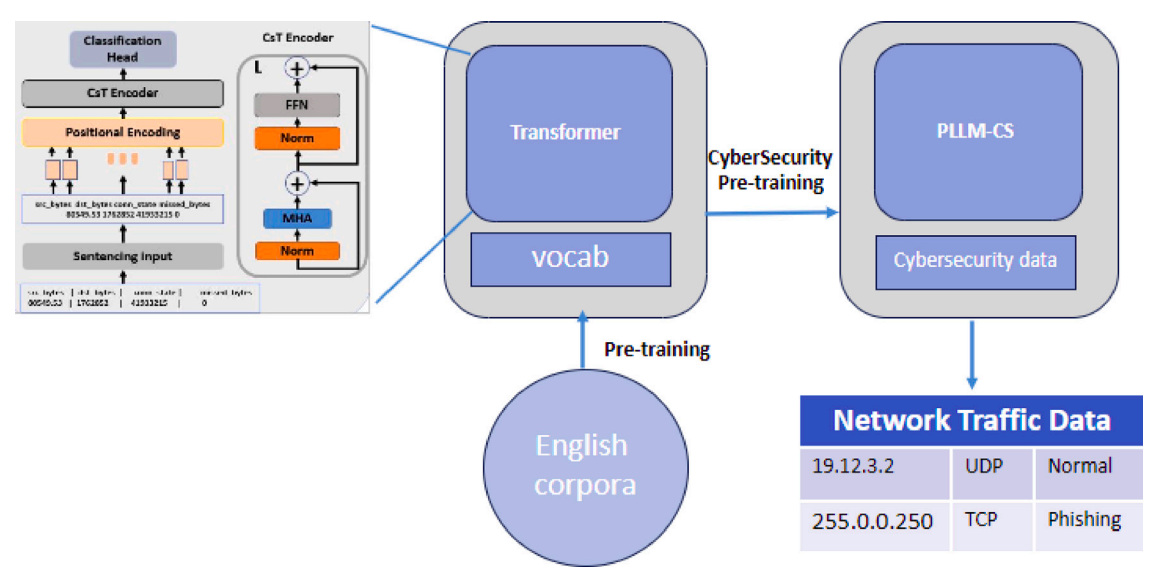 Figure: Visual explanation for PLLM-CS components. Firstly, the input is forwarded to the sentencing step to facilitate context encoding by MHA. The main contribution is to handle binary datasets with LLMs, as well as fine-tuning the parameters to achieve the highest accuracy.
Figure: Visual explanation for PLLM-CS components. Firstly, the input is forwarded to the sentencing step to facilitate context encoding by MHA. The main contribution is to handle binary datasets with LLMs, as well as fine-tuning the parameters to achieve the highest accuracy.
Main contribution or disruptive approach: The main contribution I found from the Figure is that there is a pre-training transformer and a PLLM-cs as the second training stage.
“A Comprehensive Security Framework for Wireless Sensor Networks using SHA256 and CNNs”
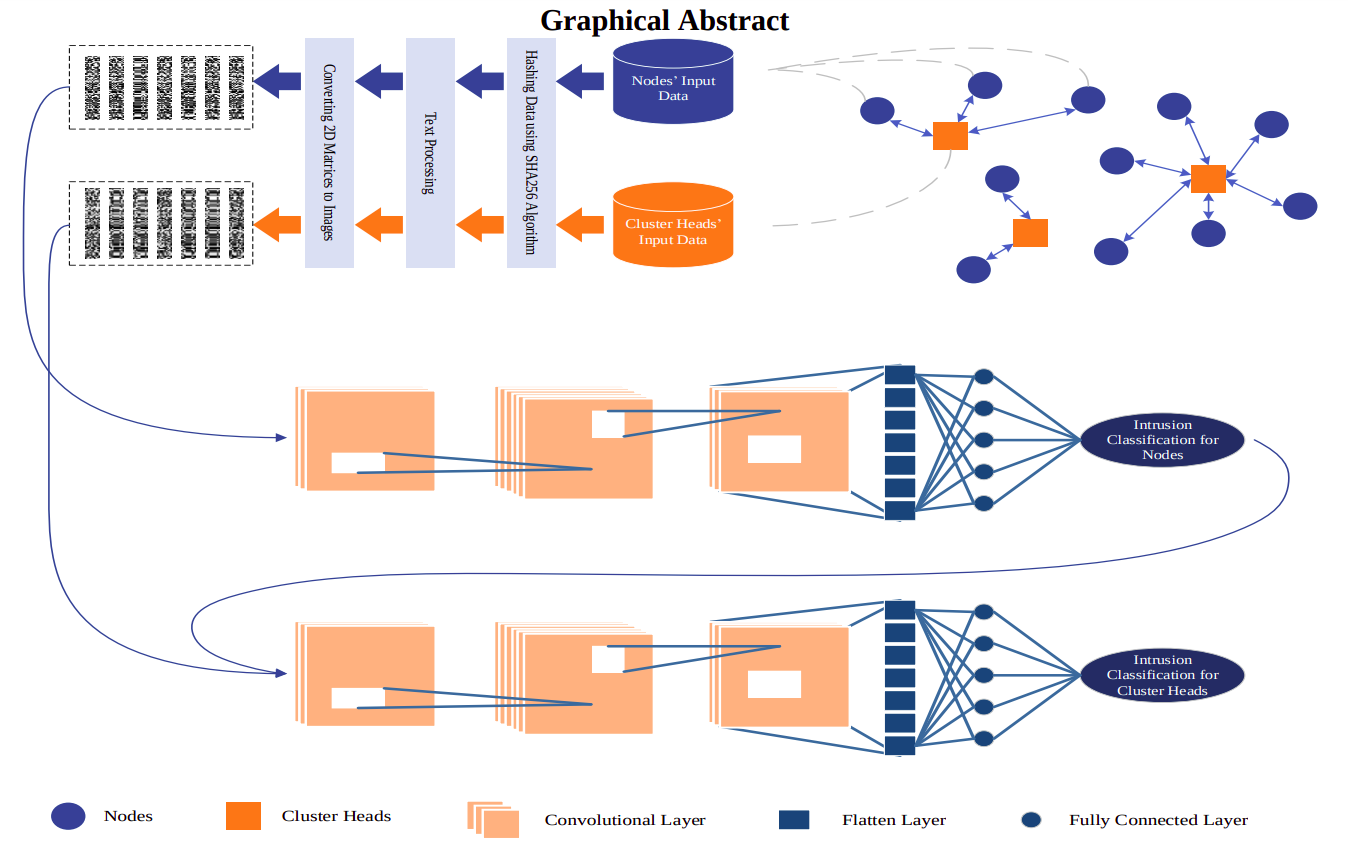
Context: Current security approaches on Wireless Sensor Networks exhibit limitations, such as inadequate granularity in addressing node and cluster head vulnerabilities, and a lack of cohesive prevention-detection strategies.
Proposal: A two-phase security method tailored for WSNs. The first phase employs Convolutional Neural Networks (CNNs) optimized with the Emperor Penguin algorithm for precise intrusion detection at the node level. The second phase extends this approach to cluster heads, forming a cohesive security framework informed by the first phase’s output.
Dataset: The Wireless Sensor Network Dataset
Main contribution or disruptive approach: The usage of special algorithm named Emperor Penguin Colony for CNN model optimization. The authors also mention the usage of encryption method SHA256 for preserving privacy on the traffic analysis. However, personally, I do not consider this point a big jump.