How to track down events [Pending]
How to track down events [Pending]
Preliminars
Some questions
- How do we label events? or how do we obtain labeled events?
- How do we associate an system event (either a network packet sent or received, a filesystem occurrence, an system access event, or system performance metrics, with a system application, process, or whatever that cause events?
- When generating an elasticsearch event, how do we track down:
- the audit logs it generate,
- the network packets it generates,
- the filesystem changes it produces,
- and the performance metrics it generates?
- With sysmon is it possible to track down up to network events?
Some answers:
- We have seen that elasticsearch can enable rules by choosing an specific tag. Therefore, we enable the rules corresponding to the tag ‘‘Tactic: Collection’’.
Which are the most interesting fields in the logs?
We proceed to load all the data streams that contain the *endpoint* index pattern.
- logs-elastic_agent.endpoint_security-default
- logs-endpoint.events.api-default
- logs-endpoint.events.file-default «< of interest »>
- logs-endpoint.events.library-default «< of interest »>
- logs-endpoint.events.network-default «< of interest »>
- logs-endpoint.events.process-default «< of interest »>
- logs-endpoint.events.registry-default «< of interest »>
- logs-endpoint.events.security-default «< of interest »>
- metrics-elastic_agent.endpoint_security-default
- metrics-endpoint.metadata-default
- metrics-endpoint.metadata_current_default
- metrics-endpoint.metrics-default
- metrics-endpoint.policy-default
We find that there are some weird issues:
We wanted to check if metrics-elastic_agent.endpoint_security-default data stream is relevant and when filtering with it, we found:
And one of the events has in the field error.message:
error fetching pid 1740: error fetching PID 1740: FillMetricsRequiringMoreAccess: error fetching process args: Not enough privileges to fetch information: OpenProcess failed: Access is denied.
and from all the indexes generated by endpoint security, these are the percentages: 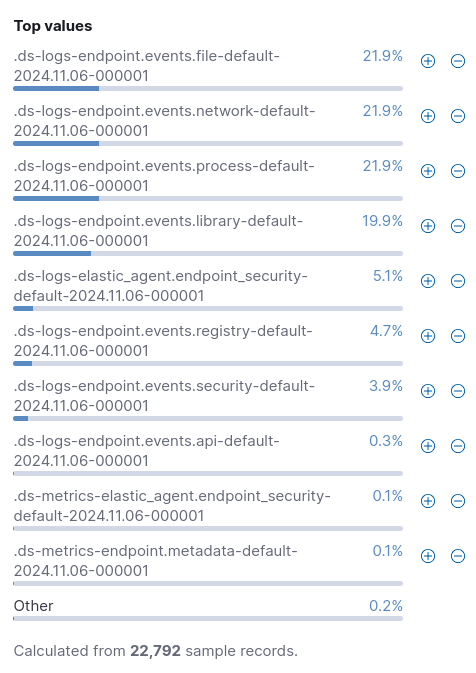
This post is licensed under CC BY 4.0 by the author.