Attempting to replicate Operation OilRig
How do we replicate OilRig?
Link: Github > Mitre > Emu
CTID Adversary EMulation Library: Link > OilRig
OilRig Link
OilRig > Emulation Plan Link
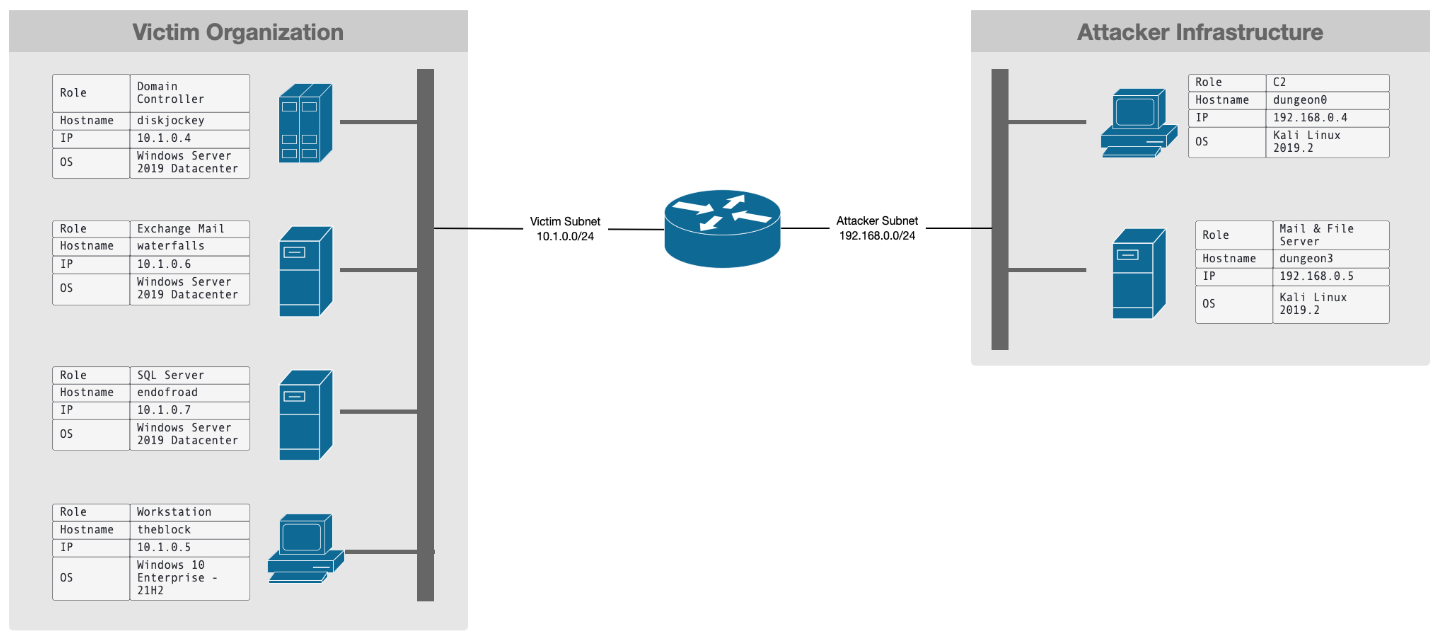
Scenario Infrastructure
Attacker infrastructure
- Attacker: Kali Linux 2019.2,
192.168.0.4 - Mail and Apache Server: Kali Linux 2019.2,
192.168.0.5
Steps performed
We downloaded the OilRig Adversary Emulation Library to the
/optdirectory.Copy VALUEVAULT (
b.exe) and TwoFace (contact.aspx) to the payload staging directory for SideTwist1 2 3
# copy VALUEVAULT (b.exe) and TwoFace (contact.aspx) to the payload staging directory for SideTwist cp Resources/Binaries/b.exe Resources/payloads/SideTwist cp Resources/Binaries/contact.aspx Resources/payloads/SideTwist
Copy
RDAT.exeto the payload staging directory for TwoFace1 2
# copy RDAT.exe to the payload staging directory for TwoFace cp Resources/Binaries/RDAT.exe Resources/payloads/TwoFace
Reference from the Github page from CTID: Link
The requirements described herein should be considered a bare minimum to execute the scenario. If you have the time and resources to remain true-to-form, you may elect to stand up multiple of each of these servers, non-contiguous IP space, etc. If you are not concerned with emulating OilRig to this degree, this level of effort is not necessary. You could for instance, phish, serve payload, and exfil from/to the same server.
- Therefore, we can:
- phish
- serve payload
- exfill from/to the same server